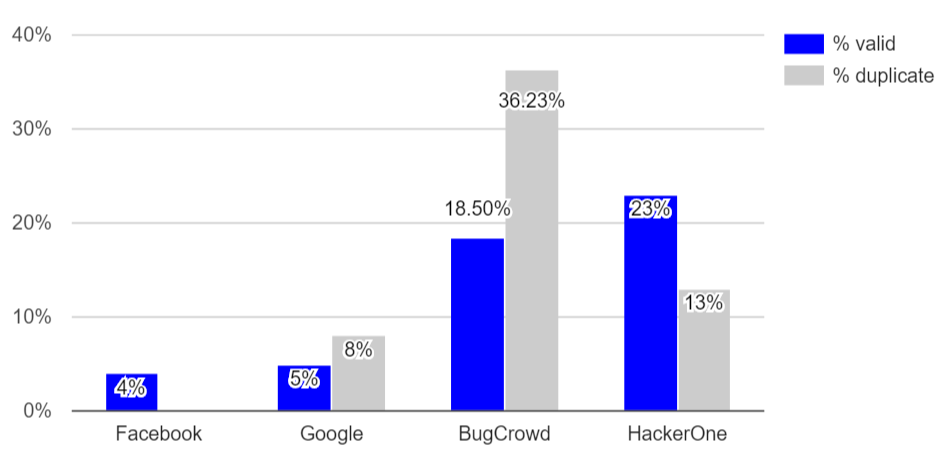
 Ratio of valid vulnerability reports can be very low, even on bug-bounty platforms.
Ratio of valid vulnerability reports can be very low, even on bug-bounty platforms.Funded in part by the National Science Foundation Award CNS-1850510
Many organizations and companies have recently chosen to use so-called bug-bounty programs (also known as vulnerability reward programs), which allow outside security experts to evaluate the security of an organization's products and services and to report security vulnerabilities in exchange for rewards. Bug-bounty programs provide unique benefits by allowing organizations to publicly signal their commitment to security and to harness the diverse expertise of thousands of security experts in an affordable way. Despite their rapidly growing popularity, bug-bounty programs are not well understood and can be mismanaged. As a result, bug bounty programs can waste substantial resources and they rarely live up to their potential to improve cybersecurity. This project will significantly improve the efficiency of bug-bounty programs by collecting and publishing comprehensive datasets on the bug-bounty ecosystem, by establishing a sound theory of bug-bounty programs, and by providing practical recommendations for organizations and regulators. The project will directly benefit organizations and companies by enabling them to manage bug-bounty programs more efficiently, which will allow them to eliminate security vulnerabilities at a lower cost; and it will also benefit users by improving the security of software products and services.
This project comprises four research thrusts. The first thrust will build a dataset that captures the entire bug-bounty ecosystem by collecting activity data and rule descriptions from public bug-bounty programs, conducting interviews and focus-group studies with experts who regularly participate in programs, collecting social-media posts, and incorporating existing datasets, such as vulnerability databases. The second thrust will analyze this dataset to understand the ecosystem and its actors' incentives and actions, and to characterize processes, such as discovering and reporting vulnerabilities and rewarding reports. To code textual data, the project will first develop a terminology and taxonomy of bug-bounty related concepts. Driven by the results of the data analysis, the third thrust will develop a formal model of the bug-bounty ecosystem, which will incorporate technological processes as well as behavioral and economic incentives. To capture all aspects of such a complex ecosystem, the project will employ models and techniques from multiple disciplines and areas, including economics and cybersecurity. Building on this model, the fourth thrust will propose and evaluate novel approaches for improving the efficiency and scalability of bug-bounty programs. The project will consider policies for individual bug-bounty programs, such as rules for rewarding vulnerability reports, as well as mechanisms for regulating bug-bounty programs and for instigating coordination between them.

 We collect high-resolution datasets from CARTA's fleet of buses, car sharing, and e-bike sharing vehicles, and analyze them using deep learning.
We collect high-resolution datasets from CARTA's fleet of buses, car sharing, and e-bike sharing vehicles, and analyze them using deep learning.Funded in part by the Department of Energy Award DE-EE0008467
The goal of this project is to develop a high-resolution system-level data capture and analysis framework to revolutionize the operational planning of a regional transportation authority, specifically the Chattanooga Area Regional Transportation Authority (CARTA). There is existing research on improving energy efficiency in transportation networks through analyzing energy consumption data per vehicle type and driving context. However, these studies are based on trip specific estimation and thus cannot be applied to a regional transportation network. Further, a number of these studies are based on simplified model estimation that is used within a simulation framework for analysis and are therefore difficult to validate during actual driving/road conditions that are not captured in the training dataset (which is typically limited in size and features).
The availability of ubiquitous high-speed networking in Chattanooga provides us with a unique opportunity to change this status quo by providing mechanisms to significantly improve the operational efficiency of fleet operations. Specifically, we collect high-resolution datasets containing all information about engine status, vehicle location, fuel usage, etc. in real-time from CARTA's fleet of buses, car sharing, and e-bike sharing vehicles and send them to a central station for analysis. Additionally, we get state of charge data from the electric vehicles, which can then be used to estimate vehicle health using data-driven prognostic algorithms developed by the team. Combined with the traffic congestion information obtained from external sources, such as HERE, this data can help create high-resolution energy consumption predictors, contextualized with features such as vehicle types and events in the city. These predictors can then be used by agencies like CARTA for operational optimization.
Overall, this project will enable the development and evaluation of tools to promote energy efficiency within a mobility-as-a-service transportation model in a mid-sized city. In addition to energy efficiency within each specific mode of operation, such as electric bus and electric car, this project will identify network mobility and energy efficiency associated with movement throughout the continuum of transportation choice present within Chattanooga. Further, the proposed project can complement the DoE national labs effort on vehicle energy consumption model by exploiting new data to investigate impacts of road/driver factors on vehicle energy consumption. In addition, the project can supplement DoE national labs efforts by providing more data on electric bus operations under various driving conditions for model validation.

 Power grids are undergoing major changes due to rapid growth in renewable energy resources, such as wind and solar power.
Power grids are undergoing major changes due to rapid growth in renewable energy resources, such as wind and solar power.Funded in part by Siemens Corporate Technology
Due to rapid growth in renewable energy resources and improvements in battery technology, power grids are undergoing major changes, which create significant management and control challenges. To tackle these challenges, decentralized solutions are needed, which can support the evolution of electrical power distribution systems. Transactive energy is a decentralized solution for dynamically balancing demand and supply, in which consumers, prosumers (i.e., consumers with energy storage or generation capabilities), providers, etc. can trade energy in an open market.
However, transactive energy solutions must also satisfy security, safety, and privacy requirements, which often seem to contradict each other. For example, to provide safety, detailed energy consumption and production information might need to be disseminated, but this threatens the privacy of prosumers. As another example, the complex and computationally expensive solutions required to provide security might not abide the real-time constraints of power systems.
In this project, we create a transactive energy system based on blockchain technology, using the distributed ledger provided by a blockchain to implement an energy trading platform. We develop protocols, smart contracts, middleware, and control algorithms to provide security, safety, and privacy for transactive energy.
Publications:
 The 2015 and 2016 cyberattacks against the Ukrainian power grid have demonstrated that remote attackers can cause significant physical impact.
The 2015 and 2016 cyberattacks against the Ukrainian power grid have demonstrated that remote attackers can cause significant physical impact.As cyber-physical systems become more prevalent, ensuring that they are resilient to cyber-attacks becomes a critical issue. For instance, cyber-physical attacks against smart water and transportation networks can pose a serious threat to public health and safety. Owing to the severity of these threats, a variety of techniques have been proposed for improving the resilience of a cyber-physical system, such as deploying redundant components and intrusion detection systems.
In this project, we explore a synergistic approach that combines multiple techniques in order to provide resilience against cyber-attacks. We study and model how the impact and feasibility of cyber-attacks depend on both the physical and cyber aspects of a system. Based on these models, we provide novel results on how to combine multiple techniques for improving resilience, considering static, dynamic, and adaptive defenses.
Publications:
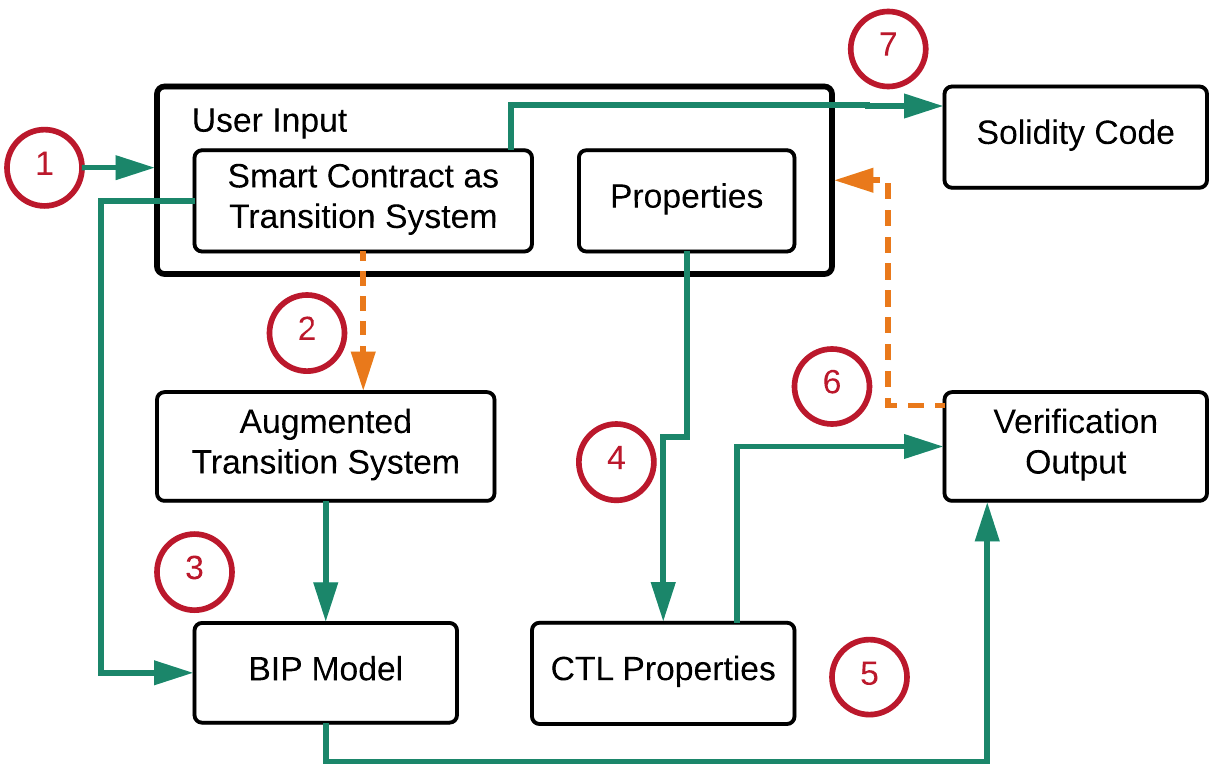 Smart contract design and verification workflow.
Smart contract design and verification workflow.The adoption of blockchain based distributed ledgers is growing fast due to their ability to provide reliability, integrity, and auditability without trusted entities. One of the key capabilities of these emerging platforms is the ability to create self-enforcing smart contracts. However, the development of smart contracts has proven to be error-prone in practice, and as a result, contracts deployed on public platforms are often riddled with security vulnerabilities. This issue is exacerbated by the design of these platforms, which forbids updating contract code and rolling back malicious transactions. In light of this, it is crucial to ensure that a smart contract is secure before deploying it and trusting it with significant amounts of cryptocurrency.
This project introduces a framework for the formal verification of contracts that are specified using a transition-system based model with rigorous operational semantics. Our model-based approach allows developers to reason about and verify contract behavior at a high level of abstraction. Our framework allows the generation of smart-contract code from the verified models, which enables the correct-by-design development of smart contracts.
Publications: